The internet is a global wide area network that connects many systems all over the world. With so many devices requiring connectivity, each one uses a specific address. As a result, the Internet Protocol address or IP address was developed to distinguish computers, routers, and websites. It is an essential component of how the internet works because it serves as an identifier for sharing information and makes devices available for communication. Furthermore, the use of IP addresses protects you from hackers and crackers gaining access to your personal information.
What is an Internet Protocol Address?
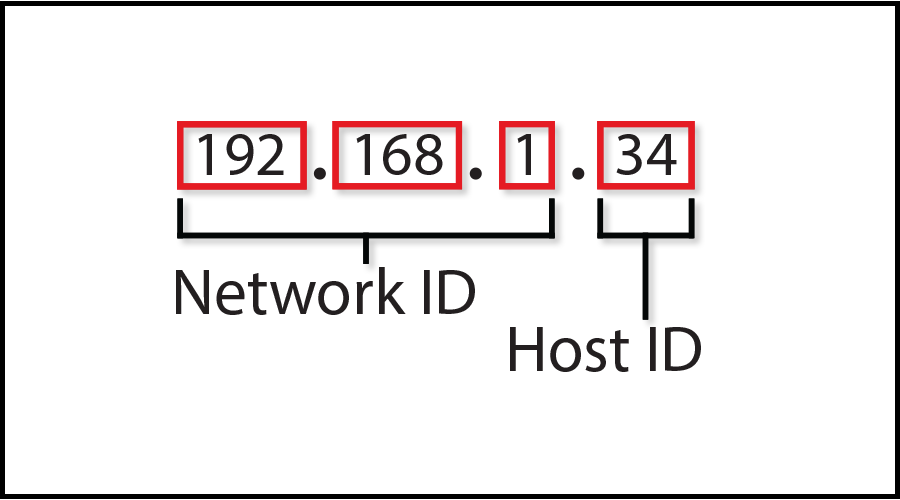
An IP address is a four-number sequence separated by periods that controls the format of data sent to the internet or a local network. The numbers range from 0 to 255, and the overall IP address ranges from 0.0.0.0 to 255.255.255.255. These numbers, however, are not chosen at random. They are mathematically organized by the Internet Corporation for Assigned Names and Numbers (ICANN) division known as the Internet Assigned Numbers Authority (IANA). Anyone wishing to register a domain name on the internet must do so through this organization.
What is the Importance of Internet Protocol Address?

Many people are unaware of how important IP addresses are because they operate behind the scenes of the internet. You may only recognize it as a string of numbers, but it serves as your networked device's identity. The system requires your IP address to connect networks, systems, and devices. It enables your device to send and receive data from other devices on a network. Consider how the Post Office requires your physical address to deliver your mail or packages.
How does Internet Protocol Address Works?
Transmission Control Protocol or TCP manages the creation of a network with two devices. But what happens if you add a new device to the network? How will you know which two computers will properly communicate? This is where the Internet Protocol enters the picture. When a new device is added to a network, it is assigned an IP address. TCP and IP work together to ensure that any two devices sharing information like source and destination can communicate.
When you connect your device to the internet, it must be connected to a network known as the Internet Service Provider or ISP. It automatically assigned an IP address to your device, allowing you to connect to the internet. Your IP address, however, varies depending on the ISP you use. The best example is when you take your device to a different location and want to connect to the internet. Your device will be assigned a different IP address based on the ISP of the restaurant, hotel, or airport you are in.
Different Types of Internet Protocol Address
IP addresses are classified into four types: private, public, static, and dynamic. However, if you want to start a website and use a web hosting service provider, you will come across two types of website addresses: shared and dedicated.
01. Private Internet Protocol Address
Every device in your home that is linked to your ISP has its own unique private IP address. Whether it's a laptop, tablet, or smartphone, and Bluetooth devices such as a speaker, printer, or watch. As a result, your router will be able to detect, identify, and differentiate them all on the network.
02. Public Internet Protocol Address
In addition to a private IP address, all devices connected to your router have a single primary public address. It is provided by your ISP to identify your network and any other devices connected outside the internet network. ISPs typically assign multiple IP addresses to each customer to monitor internet activities. They can easily track anyone who has engaged in any illegal activity on the internet.
03. Dynamic Internet Protocol Address
It is a type of public IP address that changes regularly. Your ISP will usually provide you with a dynamic IP address for your safety and security. When your IP address changes frequently, hackers and crackers find it difficult to detect your network.
Furthermore, because your ISP recycles them, dynamic IP addresses are less expensive and easier to maintain. Your previous IP address will be assigned to other customers for use. This process is automated, so there is no need to re-configure it before you can use your new IP address.
04. Static Internet Protocol Address
The static IP address is another type of public IP address. In contrast to dynamic IP addresses, this one is consistent, which means it can last for months or even years without being changed. This is typically intended for businesses that plan to host their server.
Your business needs to have a static IP address to ensure that websites and email addresses are consistently found and associated with the same IP address. Some businesses, however, believe that having your server is a waste of time and money. Going with a web hosting company that has a large number of servers and resources is much wiser and less expensive.
05. Shared Internet Protocol Address
For sole proprietors and small businesses, sharing a server with other websites is a common scenario. You can share a server with a dozen to hundreds of websites and it will work just fine, especially if you don't get enough visitors to generate more leads and sales. Although there are consequences to not having a unique IP address, such as when a website with the same IP address as yours engages in illegal online activity. The IP address will immediately be added to blacklists, preventing visitors from accessing your website and hindering all email addresses associated with your domain from being retrieved.
06. Dedicated Internet Protocol Address
If you don't like the idea of sharing an IP address with other websites, a dedicated IP address can help your business. Aside from removing the possibility of your server being added to a blacklist, dedicated IP web hosting has several other advantages. The first is that you can access your website using your IP address rather than your domain name. This is useful when testing it out while waiting for a domain transfer.
Furthermore, having a dedicated IP address makes it easier to obtain a Secure Sockets Layer or (SSL) certificate, which allows for easier authentication, encryption, and decryption of data for a website. Although you can still use an SSL certificate with a shared IP address, you must use Server Name Identification or SNI, or your ISP must support it. Finally, having a dedicated IP address allows you to have your File Transfer Protocol (FTP) server, which allows you to share and transfer files within and outside of the network.
Different Versions of Internet Protocol Address
Aside from the various types of IP addresses, there are also two versions – IPv4 and IPv6. Let's go over them one by one to see how they differ from one another.
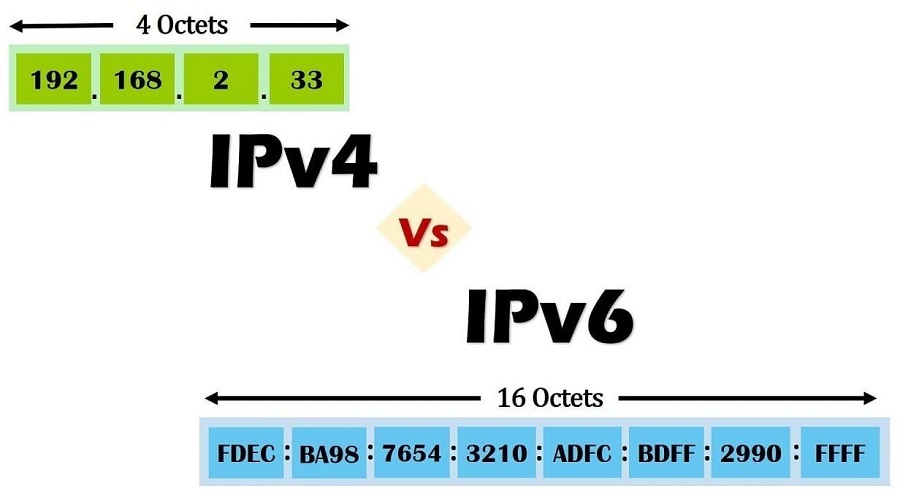
Internet Protocol version 4
IPv4, or Internet Protocol version 4, is the most common type of IP address you'll come across. An IP version 4 address is an IP address with four numbers ranging from 0.0.0.0 to 255.255.255.255 separated by periods. However, with over 4 billion IP addresses in use on the internet, it may be impossible to generate them using this version, so they created a new version of an IP address.
Internet Protocol version 6
With concerns that IPv4 will run out of addresses, IPv6 or IP version 6 is created. Some people refer to it as IPng, or IP next generation, because it provides a wider range of IP addresses. With a combination of alphabetical and numerical digits separated by colons, such as 2001:0db8:85a3:0000:0000:8a2e:0370:7334. It is also a 128-bit IP address construction that can provide more unique IP addresses in the coming years to go with an increasing number of websites and devices.
How to Detect Your Internet Protocol Address?

Do you want to find out what your IP address is? Well, that's simple. Go to Google and enter “My IP Address,” and it will display your exact public IP address. However, if you want to go further, such as discovering your ISP's name, location, and other details, you can try websites such as WhatIsMyIP.com and IPLocation. Remember to log out of your Virtual Private Network (VPN) because determining the exact location of your IP address requires a search warrant, which you must first submit to your ISP.
Finding your private IP address, on the other hand, varies depending on the device. For a Windows computer, open the command prompt, type “cmd” in the search box, and then type “ipconfig” to see the results. If you are using a Mac PC, go to System Preferences, select Network, and you will find information about your private IP address. You can also try it on your iPhone by going to Settings, selecting Wi-Fi, and then simply click the "i" in a circle next to the IP address to make it visible under the DHCP tab.
Moreover, if you have other devices on your network, you can check their IP addresses via your router. In the web browser, enter the gateway IP address of your router. Look for “Attached Devices,” which displays a complete list of the devices connected to your network as well as their IP addresses.
What are the Common Security Threats for Your Internet Protocol Address?

Since determining one's IP address is easy, protecting yours should be a top priority. With so many security threats that hackers, crackers, and other cybercriminals can perpetrate using your IP address, you must learn how to hide your IP address. But, before we get there, let's discuss the common risk of disclosing your IP address in public.
01. Social Engineering
Anyone can use social engineering to trick you into revealing your IP address. IP addresses are used by instant messaging applications such as Skype to communicate. When you use these apps to chat with someone, they can see your IP address and use the Skype Resolver tool to find your username.
02. Online Stalking
Aside from Skype, stalkers use different platforms to determine your IP address. Beginning with your internet activities such as online games, groups, forums, and more, they will be able to easily attack you. They can use your IP address to look for your location and confirm it through other social media platforms such as Facebook, Instagram, or LinkedIn.
03. Participating in Illegal Activity
The scary thing about hacked IP addresses is that hackers can engage in any illegal activity without revealing their true identity, and worse, blaming you. They have the ability to download any illegal content related to piracy, terrorism, or adult activities. This means you could get in trouble and be held accountable to the law.
04. Attacking Your Network
Directly attacking your network is one of the worst things cybercriminals can do with your IP address. The most common is a distributed denial-of-service (DDOS) attack, in which infected machines generate a large volume of traffic to your server, causing the internet to go down. Hackers frequently target online gamers because their screens are visible while streaming, revealing their IP addresses.
05. Hacking Your Device
Hackers can gain access to your device after attacking your network. Because your IP address is linked to ports, they can use this port to gain access to your device. They have the ability to steal information, install malware, and perform other types of hacks.
How to Protect Your Internet Protocol Address?

Hide your IP address if you want to keep it safe. But how are you going to do it? There are several ways to conceal your IP address, which are as follows:
01. Use a Proxy Server
If you're not familiar with a proxy server, it's what allows users to connect to the internet. It acts as an intermediary server, enabling the internet to see only the proxy server and not your actual IP address. Any information sent by the servers is routed through the proxy server before reaching you.
02. Use a Virtual Private Network (VPN)
VPN, like a proxy server, establishes a connection between you and the internet. To avoid external cybercriminal attacks, all data passes through the VPN first and hides your IP address. But the great thing about VPN is that it provides a better solution. All devices connected to a VPN act as if they are on the same network as the VPN, allowing you to access local network resources even when you are not at home. If you connect to a public Wi-Fi network or visit geo-blocked websites, using the VPN's location gives you an advantage.
03. Create Unique Passwords
Unfortunately, some people are unaware of the significance of creating unique passwords. They prefer to use default passwords because they are easier to remember, which puts them in jeopardy. Hackers can easily manipulate your device once they have access to all of your accounts. The key to avoiding this is to create passwords that are both strong and difficult to decode. To make guessing your passcode nearly impossible, try combining letters, numbers, and special characters.
04. Ignore Phishing Emails
It is critical to carefully examine the content of your emails because they may contain phishing emails. These messages contain malware or device tracking software, which can access your IP address if you click on the link or website they provide. As you may be knowledgeable, your IP address is linked to your location, name, and other personal information that can be used against you. So, if you receive emails that seem strange or irrelevant to you, it is best to ignore them. Most importantly, do not simply click any link or visit any website that may contain viruses that can harm your computer or cellphone.
05. Use an Antivirus
The last but not least option for protecting your IP address is to install a comprehensive and dependable antivirus. It is a system that protects computers and mobile devices from viruses, malware, spam or phishing emails, and other online cyber-attacks. Antivirus software protects your passwords and personal information from computer hackers who discover your IP address. There are numerous antivirus programs available to protect your online identity, including Kaspersky, Bitdefender, and Norton. Whatever you choose, remember to keep them updated to prevent new viruses from infiltrating your device.
What is Reverse IP Lookup and How Does it Work?

The reverse IP lookup is one of the technologies that is an easy, useful, and powerful way to gain new prospects and upsell existing customers. It is also known as a Domain Name System (DNS) because it determines the domain name connected to an IP address, as well as the contact number and location. Besides, reverse IP lookup shows how many times a specific IP address visits your page and how many visitors came from that IP address.
However, the information that the reverse IP lookup can retrieve is public data that is associated with a company or internet provider. Instead of detecting the exact user's name, you'll receive a visit from AT&T, Verizon, Comcast, and others. While analytic tools identify the IP address that visited your website, a reverse IP lookup can reveal the specific name hidden behind an IP address.
How Reverse IP Lookup Improves B2B Sales Prospecting?
Reverse IP lookup can help you improve your B2B sales prospecting and marketing. You can discover new potential customers by viewing the IP address along with the company and other important details. Even if not all are qualified leads, you will have a better chance of finding people who are interested in your brand. In addition, reverse IP lookup enhances lead nurturing and sales reporting. It will be easier to plan your lead nurturing activities and track leads if you know what interests your prospects.
Dynamic Leads is the best example of a lead generation software that uses reverse IP lookup. It can show who has visited your website, as well as the products and services they have viewed, using their simple and user-friendly portal. They can see your visitor's contact information, company name, and the length of time they spent on each page of your website. Aside from that, they can utilize the traffic to your website to assist you in increasing your B2B lead generation.
Start gaining insight into your audience today with Dynamic Leads!
Conclusion
Overall, the internet connection has a very complicated system. One of the things that makes it relatively simple is the Internet Protocol address. Your IP address enables your devices to connect to the internet quickly and easily. Because of the new IPv6 version, which provides more IP addresses, more devices can be connected to the internet. Your IP address, on the other hand, should be protected at all costs because it serves as your online identity. With so many hackers and crackers scouring the internet for the next victim, it pays to keep your devices secure.




